How to Setup HTTP Strict Transport Security (HSTS) for Apache
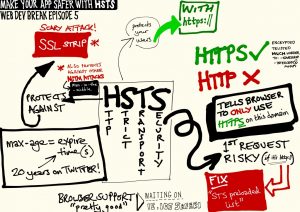
HTTP Strict Transport Security, widely known as HSTS, is a web security policy mechanism in which website tells the browser that it should only be communicated using HTTPS, instead of using HTTP Protocol. This is achieved using an HSTS response header sent at the very beginning to the browser.
The question which arises here is, why we want our website to communicate only over HTTPS Protocol???
HTTP stands for HyperText Transport Protocol, Which is just a handy way for passing information between web servers and clients. This information is transferred in form of packets over the network. Packets transferred with HTTP Protocol are not encrypted and the information contained in them can be sniffed with packet analyzer tools like Wireshark. Therefore, HTTP requests are vulnerable to Man in the middle attack (MITM) & Session Hijacking. Anyone can get in the middle by hacking a router or cutting a cable. Your ISP is already in the middle and can read, modify and misuse your HTTP communication. Sensitive information like logins to bank websites, personal portals, filling out forms with credit or debit card details should not be performed over HTTP.
HTTPS is a communication protocol for secure communication over a network. Packets transferred with HTTPS Protocol are encrypted and protected against attacks similar to Man in the middle attack (MITM) & Session Hijacking. HTTPS consists of communication over Hypertext Transfer Protocol (HTTP) within a connection encrypted by Transport Layer Security, or its predecessor, Secure Sockets Layer. The main motive for HTTPS is to maintain authentication of the visited website and protection of the privacy and integrity of the exchanged data.
Why HTTP Strict Transport Security is needed???
Even after installing SSL, some websites contain the internal pages which serve the request over HTTP, these HTTP requests are potent enough to make a big disaster. To avoid the usage of HTTP Protocol completely from a website HTTP Strict Transport Security header was introduced. It forcefully redirects the website URL to HTTPS and turns any insecure links placed inside the web application into secure links.
Implementing HSTS on Apache
I am using Ubuntu 14.04 for demonstration. You can also follow these on other flavors of Linux.

-
Enable the Apache Headers Module.
a2enmod headers
-
Add the additional line written with red color below to the HTTPS VirtualHost File.
<VirtualHost *:443>
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
ServerName mydomain.com
ServerAlias www.mydomain.com
DocumentRoot /var/www/nodeapp/
Options -Indexes
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/mydomain.com.crt
SSLCertificateKeyFile /etc/apache2/ssl/mydomain.com.key
SSLCertificateChainFile /etc/apache2/ssl/mydomain.com:3000.ca-bundle
</VirtualHost>
Understanding the max-age and includeSubDomains Directives.
max-age: Sets the time (seconds) browsers must enforce the use of HTTPS to browse the website.
includeSubDomains: Used to enforce the use of HTTPS on subdomains of your website.
-
Save and exit the file
-
Restart the Apache service
/etc/init.d/apache2 restart
Congratulations, You have just configured the HTTP Strict Transport Security on your website. Before Implementing this tutorial, Please make sure your website and all its subdomains are running over HTTPS.
Rollback HTTP Strict Transport Security
In case, the website breaks down after implementing HSTS. Just change the value of max-age directive to 0 instead of 31536000, in VirtualHost File to rollback HSTS.
Header always set Strict-Transport-Security "max-age=0; includeSubDomains"
/etc/init.d/apache2 restart
HSTS Preloading

However, when connecting to an HSTS host for the first time, the browser won’t know whether or not to use a secure connection, because it has never received an HSTS header from that host. To mitigate this attack, we have the option to preload a list of hosts on browsers like Chrome, Firefox, and Safari. One should be very careful while using the preload directive and must have gone through its pros and cons before implementing it. For the detailed description regarding preload directive usage Click Here.
Implementing Preloading
Just add the preload directive in the end of HSTS header listed in above SSL VirtualHost File.
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
/etc/init.d/apache2 restart
I hope this tutorial of mine is helpful in providing some insights regarding Apache Hardening and Security Enhancement. Like, share, and stay tuned to Linux Together for more useful articles. Cheers!



Recent Comments